Privileged Account Management
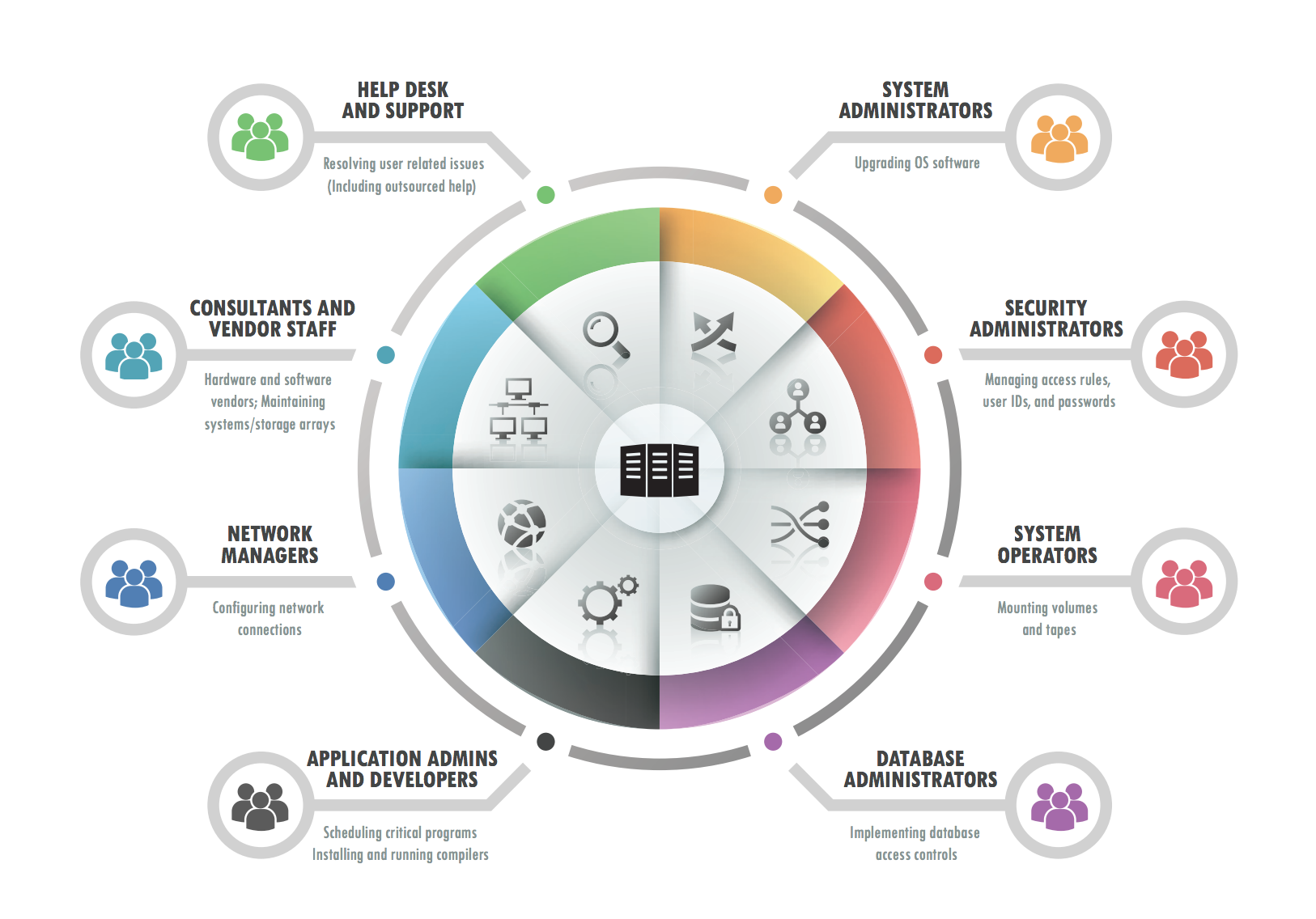
What Is Privileged Access Management Core Security

Learn About Privileged Access Management Microsoft 365 Compliance Microsoft Docs
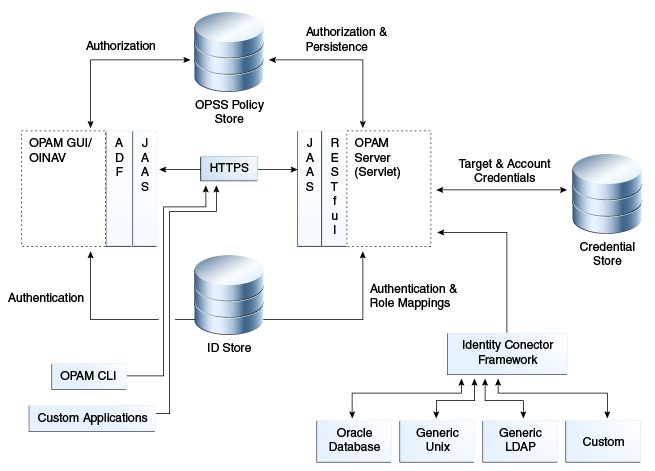
Understanding Oracle Privileged Account Manager

Secret Vault Privileged Account Management Platin Bilisim
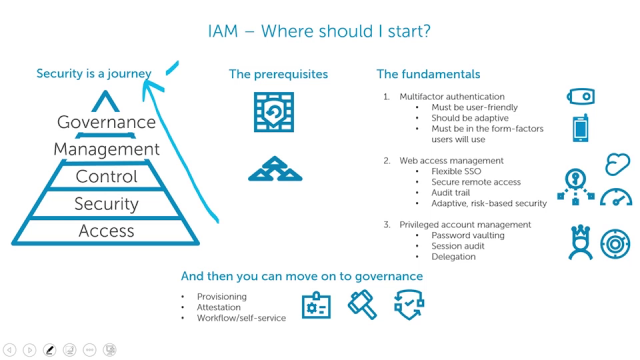
Learn Where To Start With Identity And Access Management
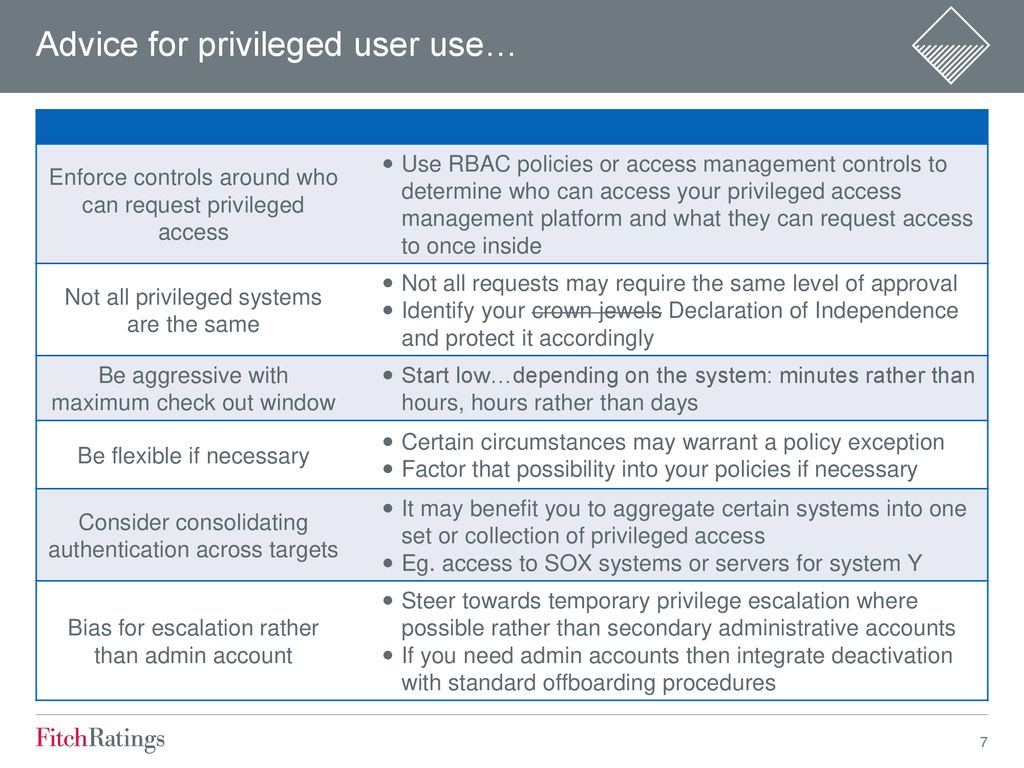
B2bsalescafe Files Wordpress Com 17 11 Market Guide For Privileged Access Management Aug 17 Pdf
In some cases, these service accounts have domain administrative privileges depending on the requirements of the application they are being used for.
Privileged account management. Limit the scope of permissions for each privileged account. Service Accounts can be privileged local or domain accounts that are used by an application or service to interact with the operating system. Defining PAM Privileged Account Management We call privileged accounts those accounts that have the most power inside an IT department and are used by the team to set up the IT infrastructure, to install new software or hardware, to run critical services or to conduct maintenance operations.
Privileged access is typically granted to system administrators, network administrators, staff performing computing account administration, or other such employees whose job duties require special privileges over a computing system or network. For instance, anyone who can set up and delete user accounts and roles on your Oracle database is a privileged user. By dialing in the appropriate level of privileged access controls, PAM helps organizations condense their organization’s attack surface, and prevent, or at least mitigate, the damage arising from external attacks as well as from insider malfeasance.
A password alone is not enough. Privileged access enables an individual to take actions which may affect computing systems, network communication, or the accounts, files, data, or processes of other users. - Safeguard privileged accounts by using two-factor authentication.
Privileged account management can be defined as managing and auditing account and data access by privileged users. Privileged Access Management accomplishes two goals:. Re-establish control over a compromised Active Directory environment by maintaining a separate bastion environment that is known to be unaffected by malicious attacks.
Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables you to manage, control, and monitor access to important resources in your organization. Ensure critical system files as well as those known to be abused by adversaries have restrictive permissions and are owned by an appropriately privileged account, especially if access is not required by users nor will inhibit system functionality. These resources include resources in Azure AD, Azure, and other Microsoft Online Services such as Microsoft 365 or Microsoft Intune.
Linux and Mac File and Directory Permissions Modification. Privileged Access Management (PAM) refers to a class of solutions that help secure, control, manage and monitor privileged access to critical assets. Privileged access management (PAM) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for users, accounts, processes, and systems across an IT environment.
There are many form factors available — hard tokens, soft tokens, push-to-authenticate/approve, NFC Bluetooth beacons, GPS/location information, fingerprints and so on.

Ciso Series Secure Your Privileged Administrative Accounts With A Phased Roadmap Microsoft Security
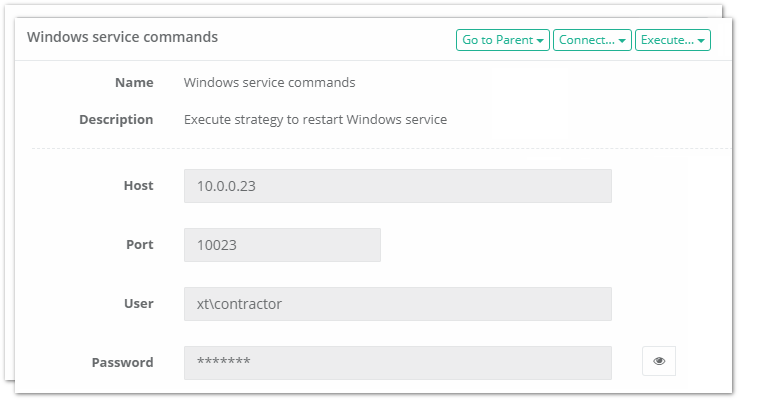
Privileged Access Management Pam Solutions Xton Technologies

What Is Privileged Account Management Manageengine Password Manager Pro

Privileged Account Security Solutions With Cyberark

Privileged Account Management Thycotic Find It Here Technology Procurement

Tech Talk Privileged Account Management Maturity Model

Privileged Access Management For Active Directory Domain Services Microsoft Docs

Privileged Access Threat Report 19 Beyondtrust

Privileged Access Management Pam Solutions Ekran System
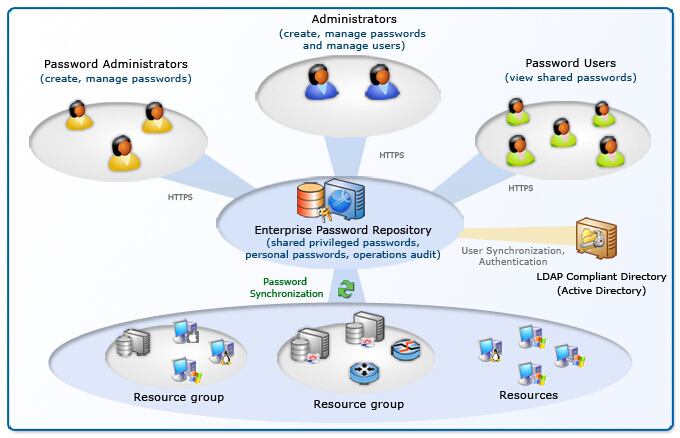
Privileged Password Management Solution Privileged User Account Manager

3 Strategic Decisions That Power Your Privileged Account Access Approach Cybersheath

Cyberark Privileged Account Management Infoguard
Infographics Ten Functions Of Privileged Account Management Xton Technologies
Privileged Account Management Best Practices

What Is Privileged Access Management Onelogin

What Is Privileged Access Management Pam Varonis
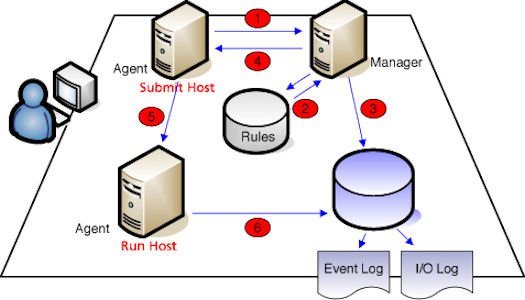
Privileged Account Manager

What Is Privileged Access Management Pam Varonis

The Security Sector To Watch Privileged Account Management By Jeffrey Feng Medium

Reports Dashboards And Analytics Bravura Privilege
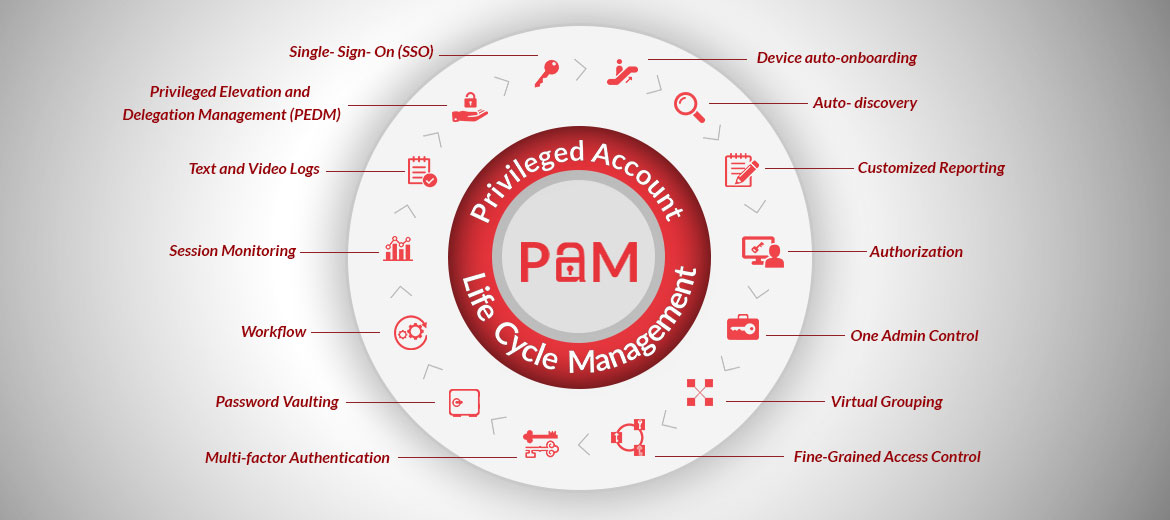
Privileged Access Management Solutions Overview

Amazon Com Privileged Account Management For The Financial Services Sector Nist Sp 1800 18 Ebook National Institute Of Standards And Technology Kindle Store

How Privileged Account Manager Solves The Business Challenges Privileged Account Manager Administration Guide

Latest Stories Published On Best Privileged Account Management Articles Medium

Privilege Account Lifecycle Management Arcon Blog
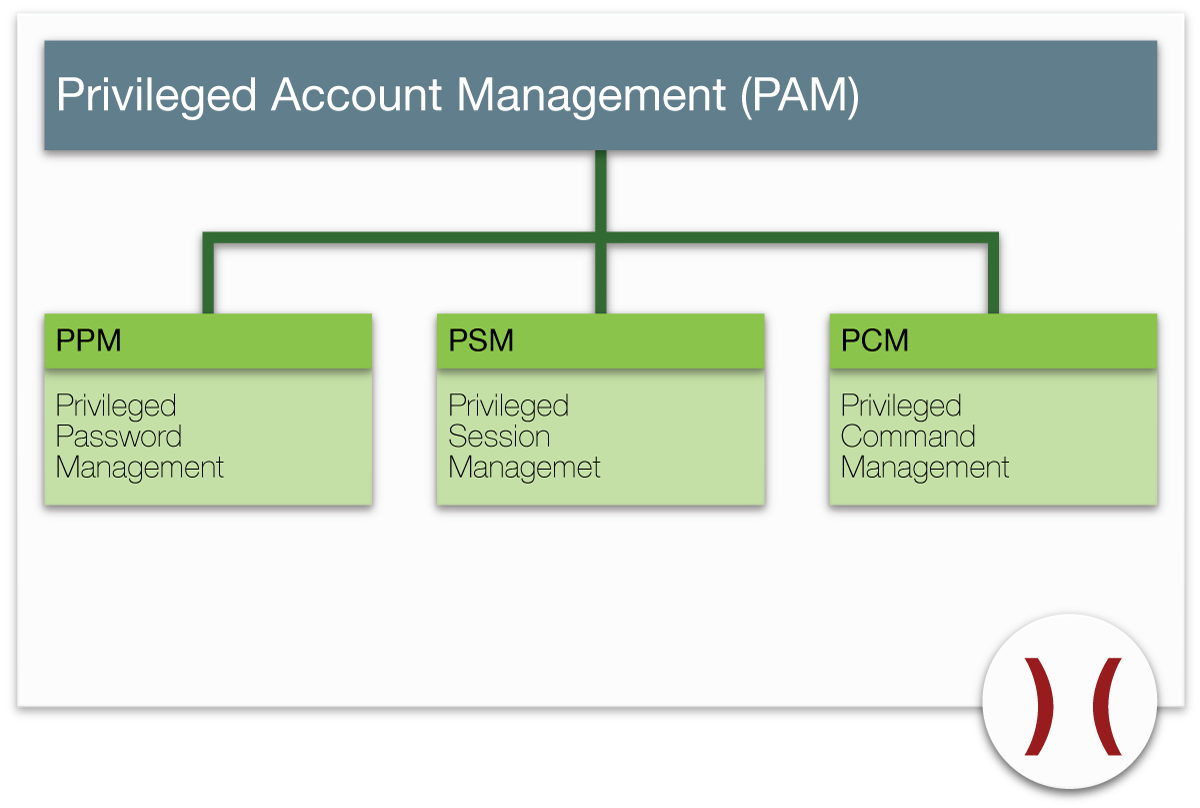
Some Thoughts About Privileged Identity Management And Privileged Account Management

Microsoft Azure S Privileged Identity Management Dev Community

Pam Market Size Worldwide Statista
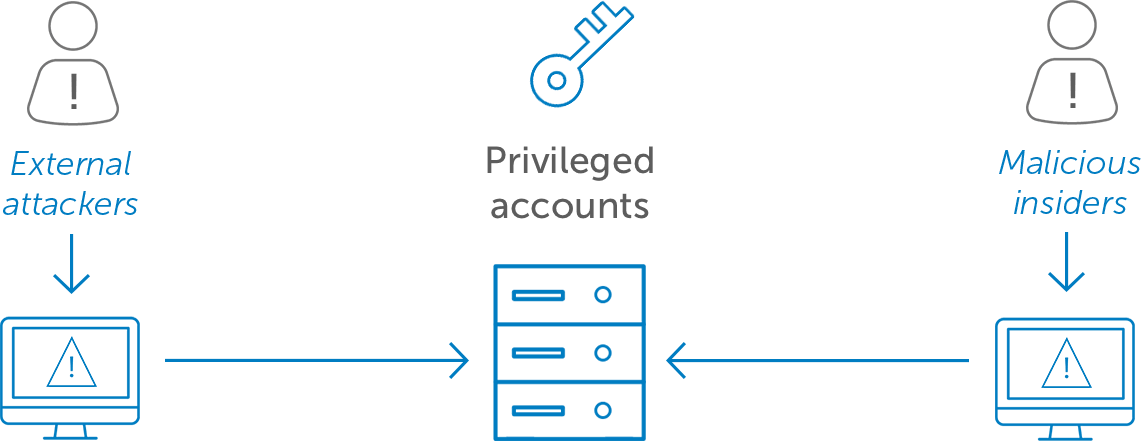
Privileged Access Management Okta

Privileged Access Management Ppt Download

What Is Privileged Access Management Security Priority 1

Privileged Account Management 1 In Gartner Top 10 Security Projects

What Is Privileged Access Management Security Priority 1

How Privileged Account Manager Solves The Business Challenges Privileged Account Manager Administration Guide

Privileged Account Management With Cyberark Don T Panic
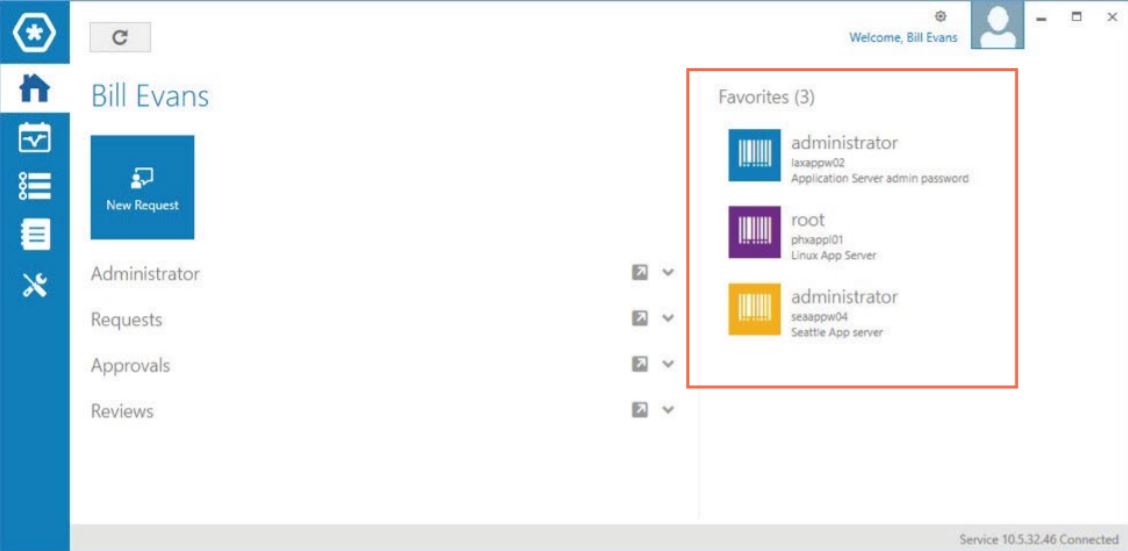
Privileged Account Management With One Identity Safeguard Corporate Solutions

What Is Privileged Account Management Pam
Q Tbn And9gcrnc1smthjizbbj9kds2igecehsrafcgcyawyjytan2vuxatk Usqp Cau

Privileged Account Management Is Critical For Information Security

Shows How Privileged Access Management Pam Helps To Address Five Download Scientific Diagram

How To Manage Privileged Accounts And Identities Micro Focus Community

Pdf Privileged Account Management Approach For Preventing Insider Attacks
Q Tbn And9gctpjnb9hbyz6uq354eupuksflw5vrl 4yn Xu6gaae Usqp Cau

Cyberark
Q Tbn And9gcra3bbhof R0q9celbr14idqicmddrf9hwgenqk1a Bl D9qcom Usqp Cau
1

7 Most Common Privileged User Management Systems The Techeries
Privileged Account Management 101 How Can Privileged Accounts Compromise Your Security

Different Paths Same Goal Privileged Account And Session Management Pasm And Privilege Elevation And Delegation Management Pedm

Privileged Access Management Pam Is The 1 Cyber Security Priority
The Seven Keys To A Successful Privileged Account Management Strategy Kuppingercole
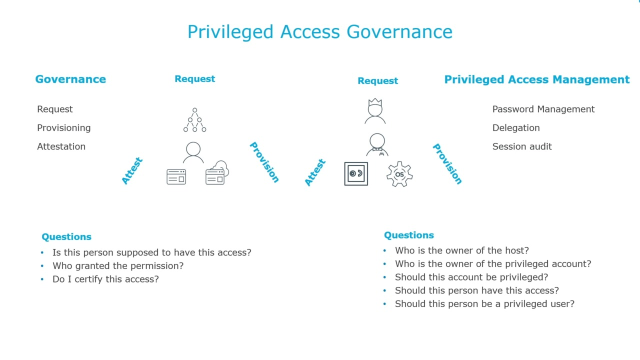
Privileged Access Governance

Implementing Privileged Access Management Pam The Pam Lifecycle
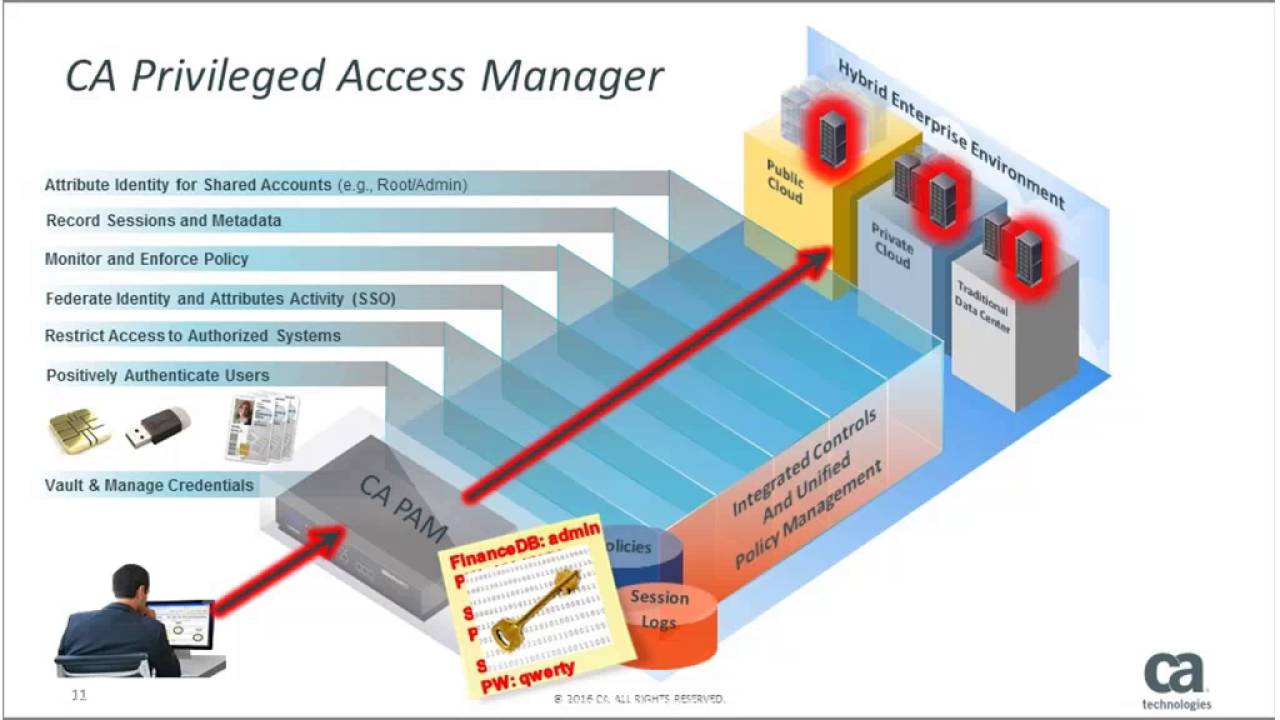
What Is Ca Privileged Access Manager Definition From Whatis Com

The Top 10 Privileged Access Management Pam Solutions Expert Insights

Pam Deployment Is Challenging And Requires Well Managed Projects

Privileged Access Management Pam Zero Trust Privilege Service Centrify
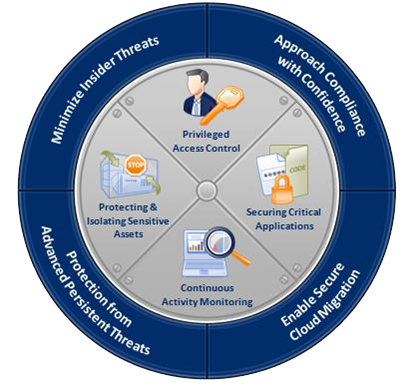
Privilege Access Management

What Is Privileged Access Management Pam Varonis

Top 5 Poor Privileged Account Management Practices Ekran System

Why Privileged Access Management Is Essential For All Businesses Patecco En

Privileged Access Management In Office 365 Is Now Generally Available Microsoft Tech Community

Privileged Access Management Netiq Privileged Account Manager Micro Focus
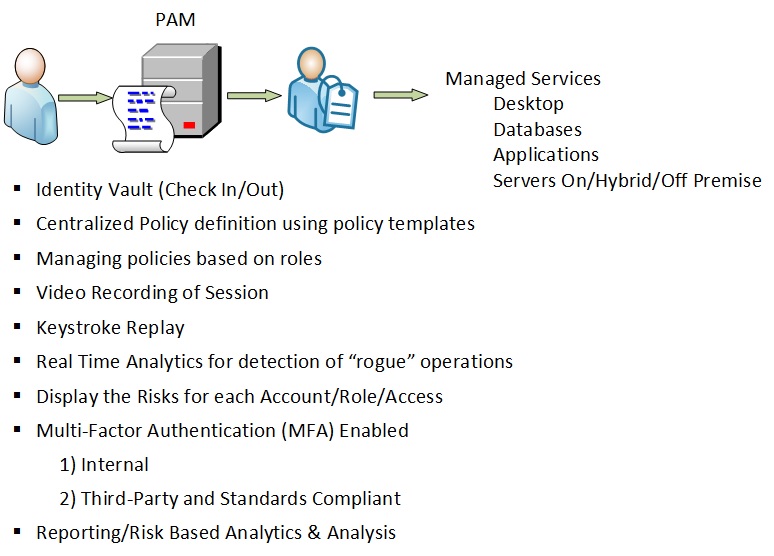
Privileged Access Management Pam Best Practices

Managing The Keys To The Kingdom Privileged Shared Accounts Simeio Solutions Oracle Cloud Security Blog

Why Privileged Access Management Pam Should Be Cisos Top Priority

Tech Talk Privileged Account Management Maturity Model

What Is Privileged Access Management Pam Explained Security Wiki

Can Privileged Account Management Really Stop Credential Theft Javelin Networks Blog

Privileged Account Management 101 How Can Privileged Accounts Compromise Your Security

Application Model For Privileged Account Access Control System In Enterprise Networks Sciencedirect
The Components Of Privileged Account Management Process Download Scientific Diagram
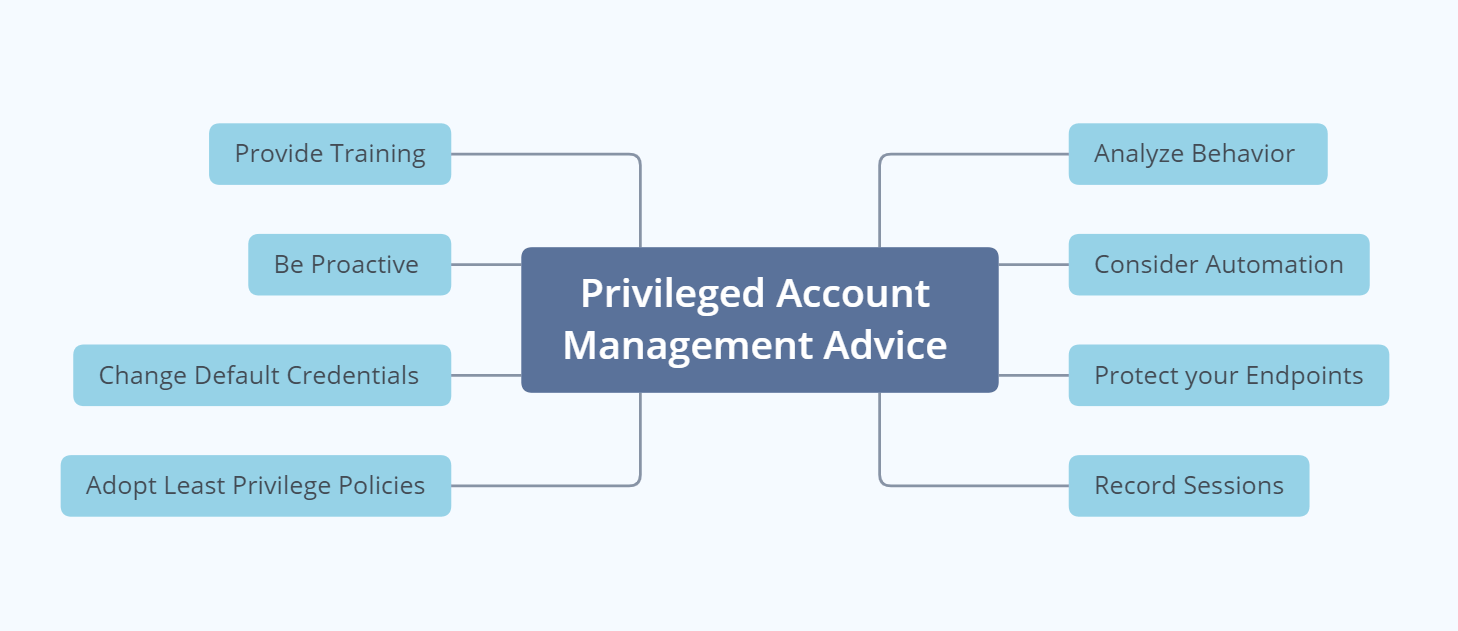
Privileged Account Management 101 How Can Privileged Accounts Compromise Your Security
Privileged Access Management For Windows Active Directory Domains
Findings Gartner Magic Quadrant For Privileged Access Management
Cyberark Privileged Account Management Wwt

Privileged Access Management For Active Directory Domain Services Microsoft Docs
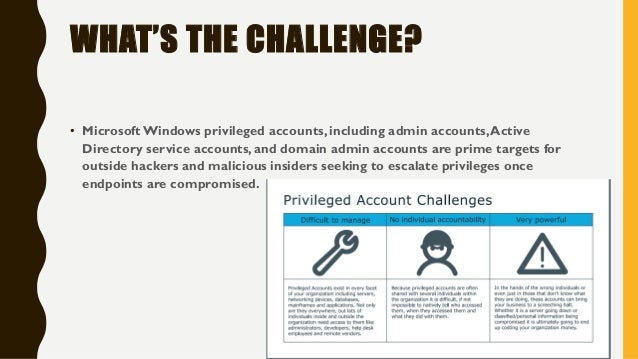
10 Steps To Better Windows Privileged Access Management

Cst Thycotic Privileged Account Management For Dummies

What Is Privileged Access Management Pam Read The Definition In Our Security Glossary Beyondtrust

One Identity Manager Privileged Account Governance 3 Safeguard User Management Youtube

Privilege Account Management Solidfish
Www Nccoe Nist Gov Sites Default Files Library Project Descriptions Fs Pam Project Description Draft Pdf
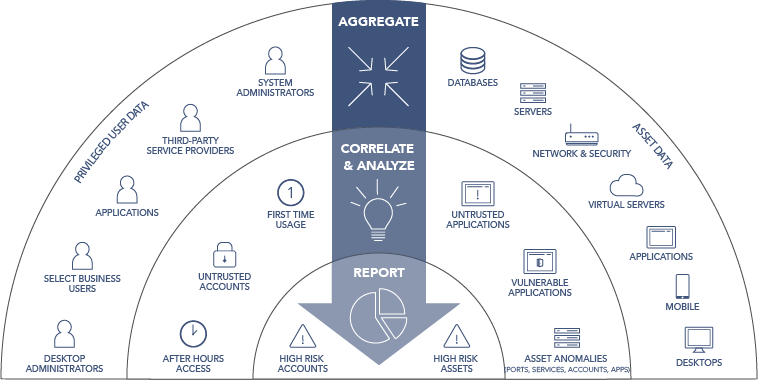
What Is Privileged Access Management Pam Read The Definition In Our Security Glossary Beyondtrust

Capability Framework For Privileged Access Management

Breaches Are Inevitable Adding Resiliency To Your Pam Program Technology Insights Blog

Privileged People And Powerful Systems Balancing Trust With Thycotic Techhq

A Seven Step Process To More Effective Privileged Account Management
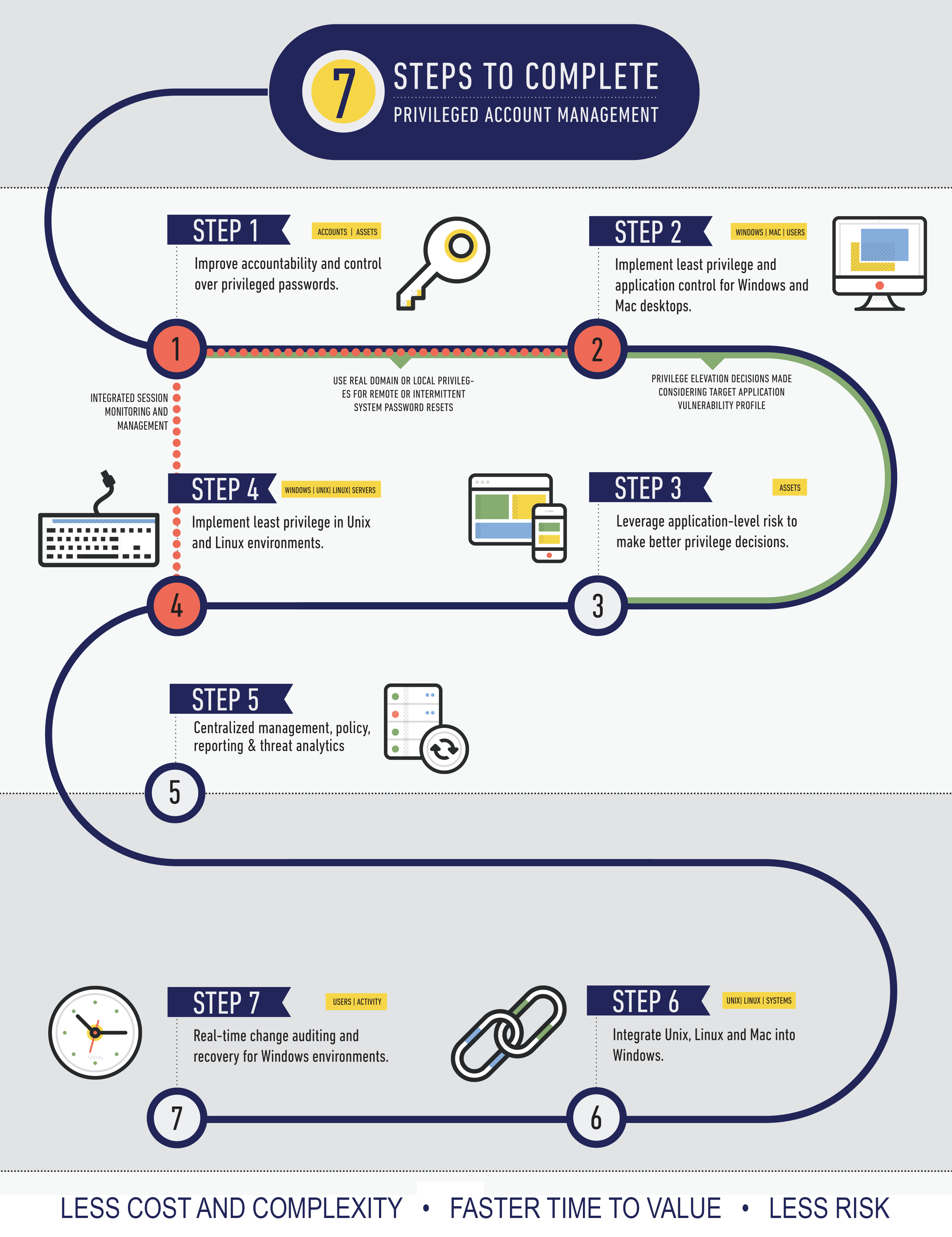
Where To Begin A 7 Step Strategy To Achieving Complete Privileged Account Manag Beyondtrust

What Is Privileged Account Management Pam

Cyberark Is4u

What Is Privileged Account Management Manageengine Password Manager Pro
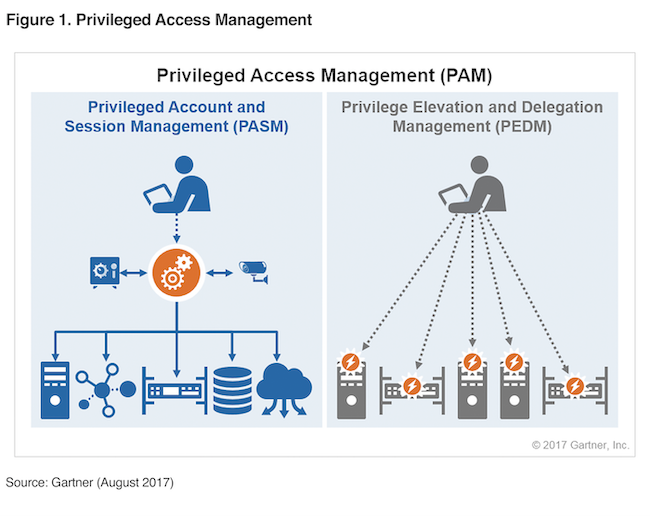
Privileged Account Management A Mandatory Requirement A Dnext
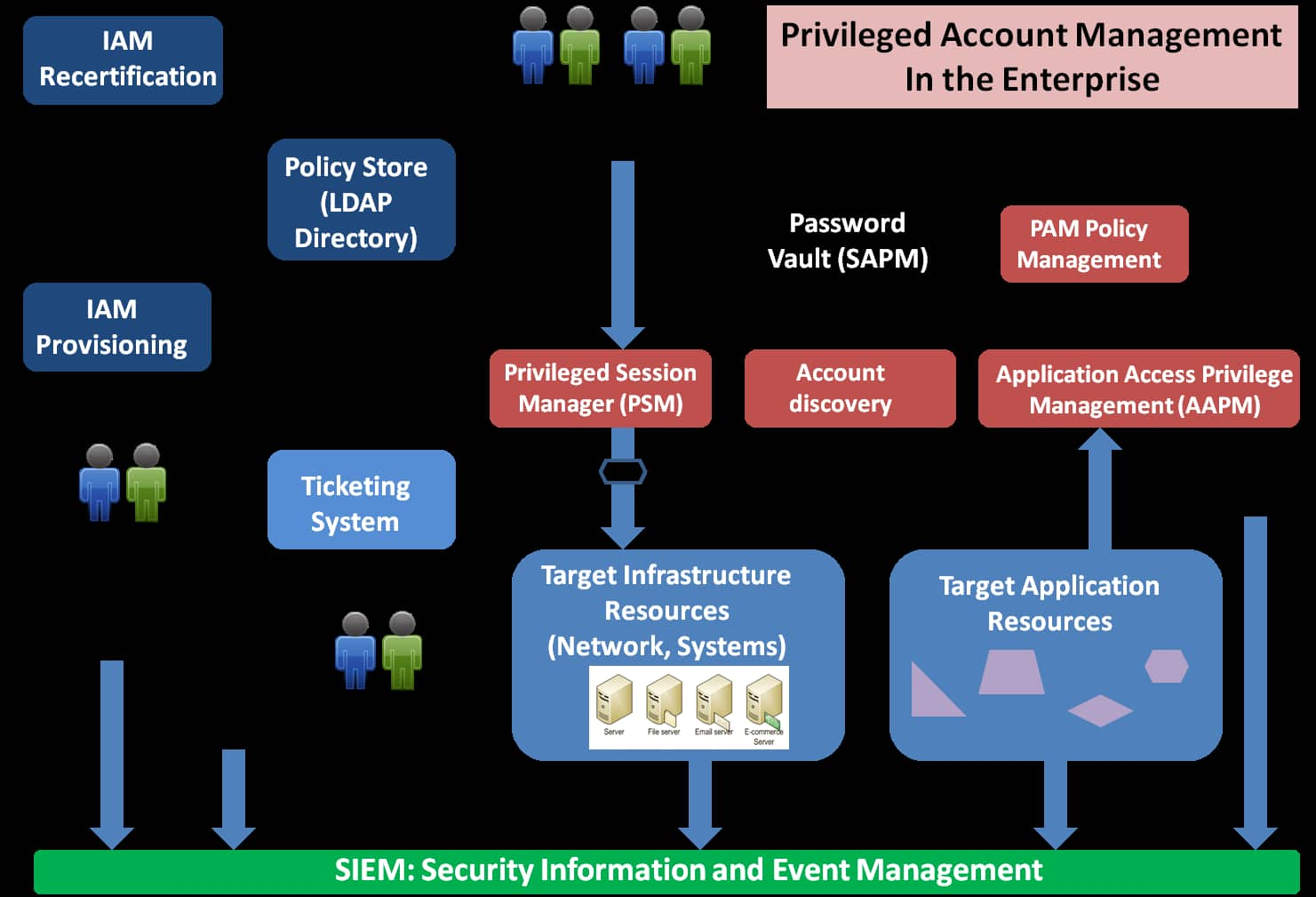
7 Essential Features Of A Perfect Privileged Access Management Solution

19 Zero Trust Privilege Maturity Model Episode 1

Password Management Solution For Privileged Account Management Session Management Remote Access Management Management Accounting Solutions

What Is Privileged Access Management Core Security
Http Wearearmadillo Com Wp Content Uploads 17 11 Cyberark Privileged Account Security Pdf



